Elevate Your IAM Effectiveness





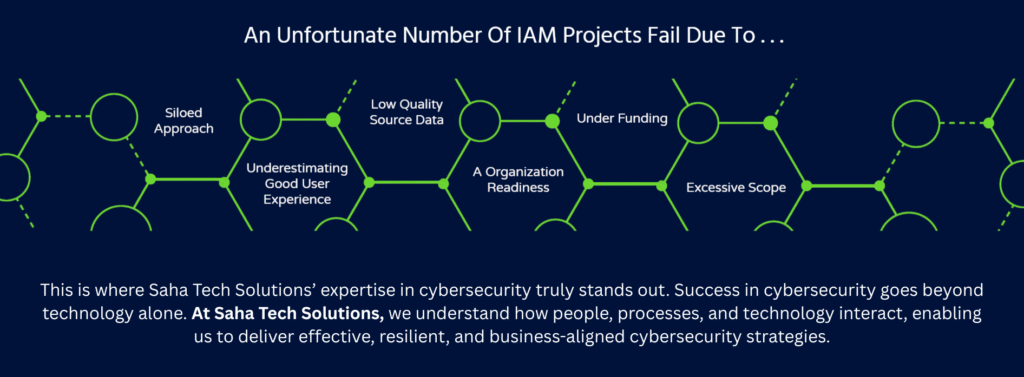
Saha Tech Solutions is a global firm specializing in cybersecurity, identity governance, and risk consulting. We partner with organizations to solve complex security, compliance, and technology challenges, while delivering strategy, transformation, and long-term management of cybersecurity and IAM programs.
info@sahatechsolutions.com
© 2025 Created with Saha Tech Solutions